AUTHENTICATION IN OBIEE
Some authentication methods used by Oracle BI server are
- Database
- LDAP
- Oracle BI server (repository users) – I do not recommend this method for medium to large implementations. It will be difficult to manage.
I will discuss on setting up LDAP in this article.
SETTING UP LDAP OR WINDOWS ADSI IN OBIEE
Microsoft ADSI (Active Directory Service Interface) is Microsoft version of LDAP server. Most of the steps to setup of either Microsoft ADSI or LDAP server are similar. In either case, you would need help from your network security group/admin to configure LDAP. They should provide you with the following information regarding the LDAP server
- LDAP server host name
- LDAP Server port number
- Base DN
- Bind DN
- Bind Password
- LDAP version
- Domain identifier, if any
- User name attribute type (in most cases this is default)
REGISTERING AN LDAP SERVER IN OBIEE
In Oracle BI repository, go to manage security.
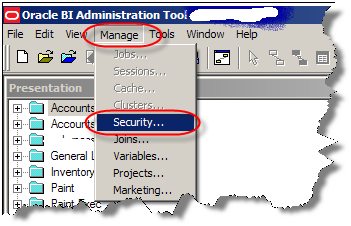
Create a new LDAP server in OBIEE Security Manager
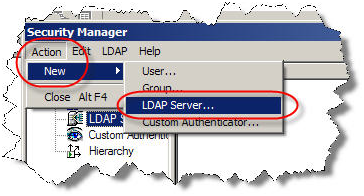
With the help from your network security group/administration, fill out the following information
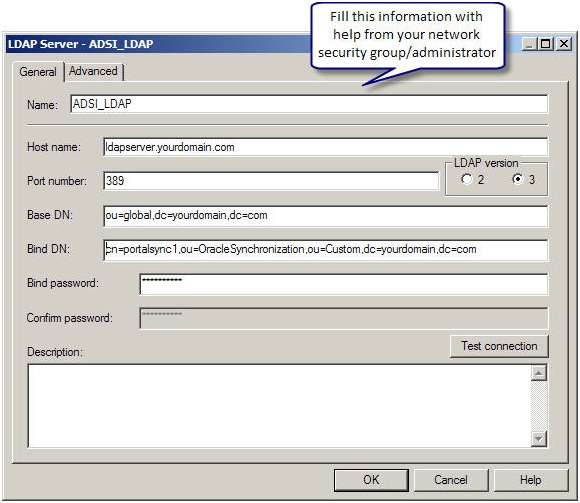
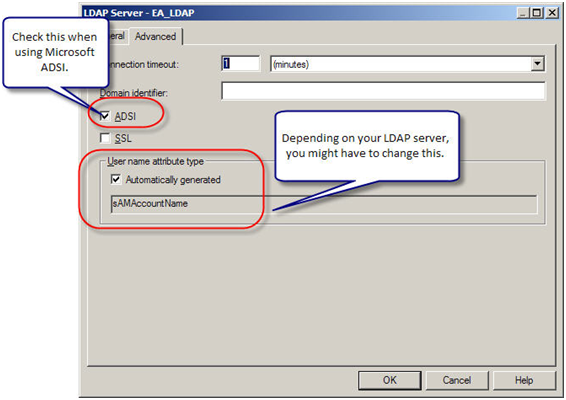
Next in the Advanced tab, based on the kind of LDAP server you have and its configuration, make the necessary changes.
For Microsoft ADSI (Active Directory Service Interface), choose ADSI and for all others leave it unchecked.
Most of the times, Username attribute would be automatically generated. For Microsoft ADSI It is sAMAccountName; for most of the LDAP servers it is uid or cn. Check with your network security group/administrator on what is the username attribute for your LDAP server. Make a note of the user name attribute you will need it later.
Now we need to create an Authentication initialization block. In administration tool, under Manage go to Variables.
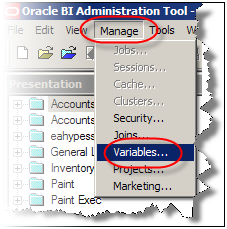
Under Action, go to New -> Session -> Initialization Block
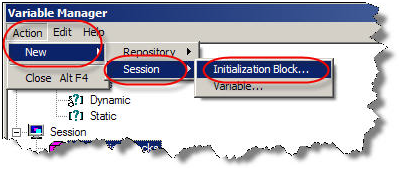
Configure the session initialization block. Give it a name and click on Edit Data Source. In the pop up window, choose LDAP from the drop down box and then click on Browse. You can also configure a LDAP server here by clicking on “New”. In the browse pop up window choose the LDAP server you would like to use.
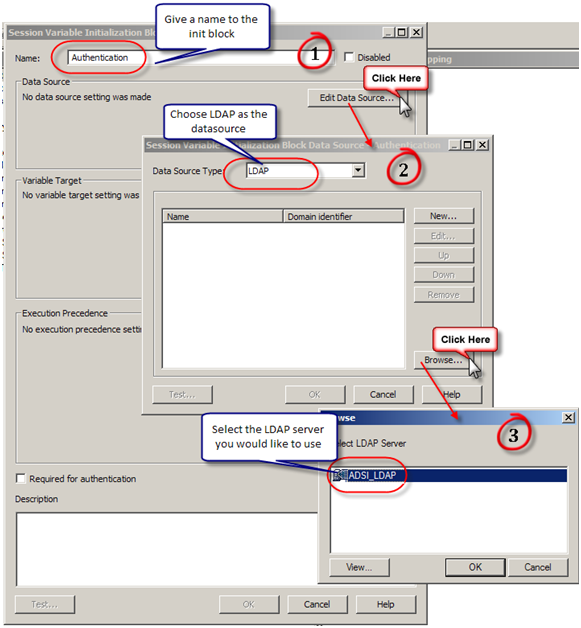
Next we need to create variables. User and Email are the common variables normally in play.
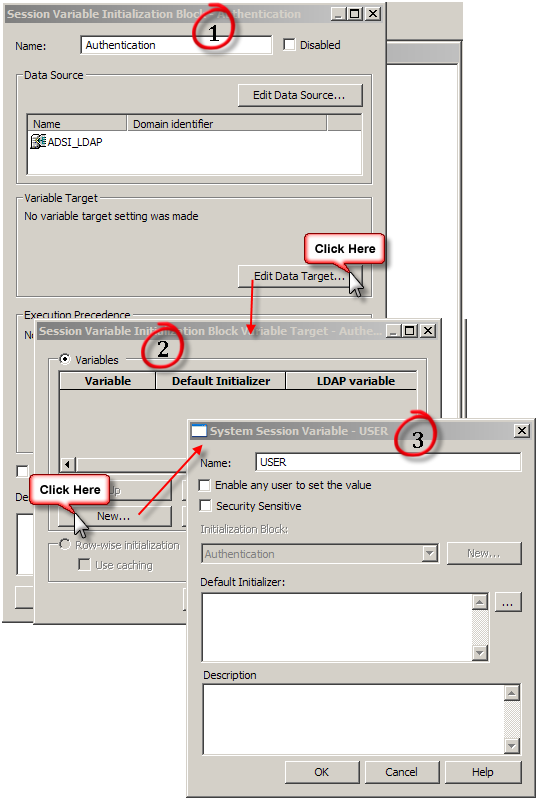
Upon clicking on OK, a warning pops up on the usage of User session variable (User session variable has a special purpose. Are you sure you want to use this name). Click yes.
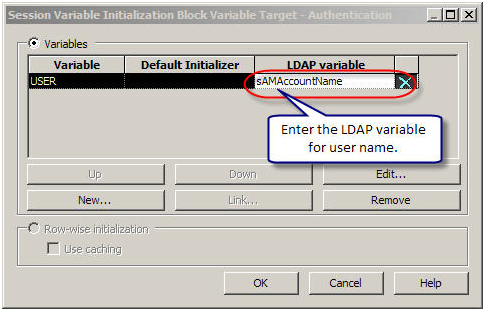
Next enter the LDAP variable for username. sAMAccountName in the case of ADSI as configured in the LDAP.
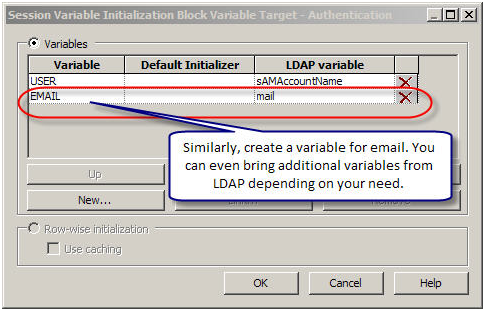
Next following similar steps create a variable for Email. In addition, depending on you need, you can bring additional variables from the LDAP server.
Now bounce your services.
No comments:
Post a Comment